Data security best practices are essential for protecting sensitive information in today’s digital age. In this guide, we will explore the key strategies to ensure the security of your data and prevent potential breaches.
From encryption to access control measures, we delve into the best practices that every organization should implement to safeguard their valuable data assets.
Importance of Data Security
Data security is a critical aspect for businesses in today’s digital age. With the increasing amount of sensitive information stored online, protecting data from unauthorized access, breaches, and cyber threats is essential to maintain trust with customers, comply with regulations, and safeguard the organization’s reputation and financial stability.
Consequences of Poor Data Security Practices
Poor data security practices can have severe consequences for businesses. One major impact is the risk of data breaches, which can result in the exposure of sensitive information such as customer data, financial records, and intellectual property. This can lead to legal repercussions, financial losses, and damage to the organization’s reputation.
Data breaches can also lead to a loss of customer trust and loyalty. When customers’ personal information is compromised, they may lose confidence in the organization’s ability to protect their data, leading to a loss of business and potential lawsuits. Moreover, data breaches can also result in regulatory fines and penalties for non-compliance with data protection laws.
Impact on Organization’s Reputation and Financial Stability
A data breach can have a significant impact on an organization’s reputation and financial stability. The negative publicity surrounding a breach can damage the organization’s brand image and credibility, leading to a loss of customer trust and loyalty. This can result in decreased sales, customer churn, and difficulty attracting new customers.
Financially, data breaches can be costly for organizations to remediate. From investigating the breach, notifying affected individuals, implementing security measures, and potential legal fees and settlements, the financial impact of a breach can be substantial. Additionally, organizations may face fines and penalties from regulatory authorities for failing to protect sensitive data adequately.
In conclusion, data security is not just a technology issue but a critical aspect of business operations that can have far-reaching consequences if not adequately addressed. Implementing robust data security practices is essential to protect sensitive information, maintain customer trust, and safeguard the organization’s reputation and financial stability.
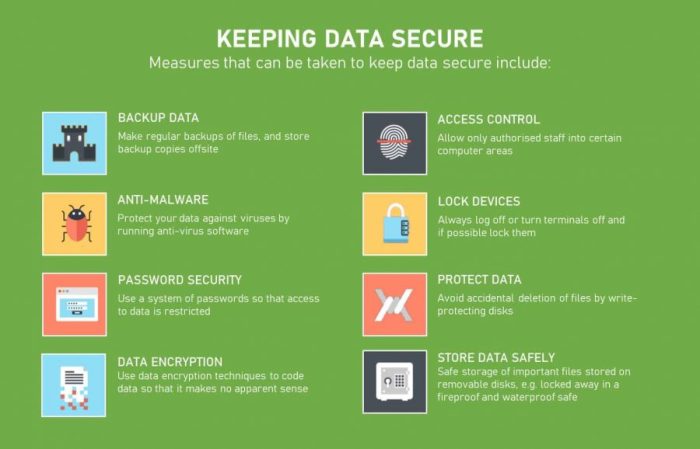
Data Security Best Practices

Data security best practices are crucial for safeguarding sensitive information and preventing unauthorized access or data breaches. Implementing robust security measures can help organizations protect their data assets and maintain the trust of their customers and stakeholders.
Importance of Encryption in Data Security
Encryption plays a vital role in data security by encoding data in a way that only authorized parties can access it. By converting data into an unreadable format, encryption ensures that even if data is intercepted, it remains protected. Utilizing strong encryption algorithms and keys is essential to maintaining the confidentiality and integrity of sensitive information.
Significance of Access Control and User Authentication Measures
Access control and user authentication are key components of data security best practices. By implementing access controls, organizations can restrict access to sensitive data based on user roles and permissions. User authentication, such as passwords, biometrics, or multi-factor authentication, helps verify the identity of users before granting access to confidential information. These measures ensure that only authorized individuals can view or modify data, reducing the risk of data breaches and unauthorized access.
Data Backup and Recovery: Data Security Best Practices
Data backup and recovery are essential components of a robust data security strategy. Regular backups help protect against data loss, whether due to accidental deletion, hardware failure, or cyberattacks. In the event of a security breach or data loss, having a reliable backup system in place can make all the difference in restoring lost data and minimizing downtime.
Importance of Regular Data Backups
- Regular data backups ensure that important files and information are safe and can be easily recovered.
- Backups provide a safety net in case of data corruption, accidental deletion, or ransomware attacks.
- By maintaining up-to-date backups, organizations can reduce the risk of significant data loss and associated costs.
Best Practices for Data Backup Frequency and Storage
- Set up automated backups on a regular schedule, depending on the frequency of data changes and the criticality of the information.
- Consider daily backups for highly sensitive data and weekly or monthly backups for less critical information.
- Store backups in multiple locations, including on-premises servers, cloud storage, and offline storage devices to ensure redundancy.
- Encrypt backup data to protect sensitive information from unauthorized access.
Strategies for Data Recovery
- Establish a clear data recovery plan outlining the steps to take in case of a security breach or data loss.
- Test data recovery procedures regularly to ensure that backups are valid and can be successfully restored.
- Consider using specialized data recovery tools and services to help recover lost or corrupted data effectively.
- Work with cybersecurity experts to investigate the cause of a security breach and implement measures to prevent future incidents.
Employee Training and Awareness

Employee training and awareness play a crucial role in maintaining data security within an organization. Employees are often the first line of defense against cyber threats and data breaches, making it essential to provide them with the necessary knowledge and skills to protect sensitive information.
Role of Employees in Maintaining Data Security
- Employees are responsible for handling and accessing sensitive data, making them key players in maintaining data security.
- By following security protocols and best practices, employees can prevent unauthorized access and data leaks.
- Training employees on how to recognize phishing attempts, malware, and other cyber threats can significantly reduce the risk of security incidents.
Examples of Security Awareness Training Programs
- Simulated phishing exercises to test employees’ ability to identify phishing emails and respond appropriately.
- Security workshops and seminars to educate employees on the latest cyber threats and security measures.
- Regular security updates and reminders to reinforce good security practices and keep employees informed about potential risks.
Importance of Creating a Culture of Security
- Establishing a culture of security within the organization encourages all employees to prioritize data protection in their daily activities.
- When security is ingrained in the company culture, employees are more likely to be vigilant and proactive in safeguarding sensitive information.
- A strong security culture can help build trust with customers and business partners, showcasing the organization’s commitment to data security.
Secure Network Practices

Securing networks is crucial in safeguarding data from unauthorized access, breaches, and cyber threats. Implementing robust network security measures helps in maintaining the confidentiality, integrity, and availability of sensitive information.
Securing Wi-Fi Networks
- Change default SSID and password: Use unique and strong passwords to prevent unauthorized access to your Wi-Fi network.
- Enable encryption: Use WPA3 or WPA2 encryption protocols to protect data in transit over the wireless network.
- Disable SSID broadcasting: Conceal your network’s SSID to make it less visible to potential attackers.
- Implement MAC address filtering: Allow only specific devices to connect to your Wi-Fi network based on their MAC addresses.
Implementing Firewalls and Intrusion Detection Systems, Data security best practices
Firewalls act as a barrier between your internal network and external threats, filtering incoming and outgoing network traffic. Intrusion detection systems monitor network activities for signs of malicious behavior, alerting administrators to potential security incidents. By deploying firewalls and intrusion detection systems, organizations can proactively identify and mitigate security threats to their networks.
As we conclude our discussion on data security best practices, it is evident that a proactive approach to data protection is paramount in safeguarding against potential threats. By following these guidelines, you can enhance your organization’s security posture and mitigate risks effectively.
When analyzing a company’s performance, it is crucial to consider various financial performance metrics such as revenue growth, profit margin, and return on investment. These indicators provide valuable insights into the overall health of the business and help stakeholders make informed decisions.
In today’s data-driven world, data science and analytics play a key role in extracting valuable insights from large datasets. By leveraging advanced algorithms and statistical techniques, companies can uncover trends, patterns, and correlations that drive business growth and innovation.
Implementing an effective OKR software can help organizations align their objectives and key results, track progress, and drive performance improvements. By setting clear goals and regularly monitoring performance metrics, companies can stay agile and focused on achieving strategic objectives.